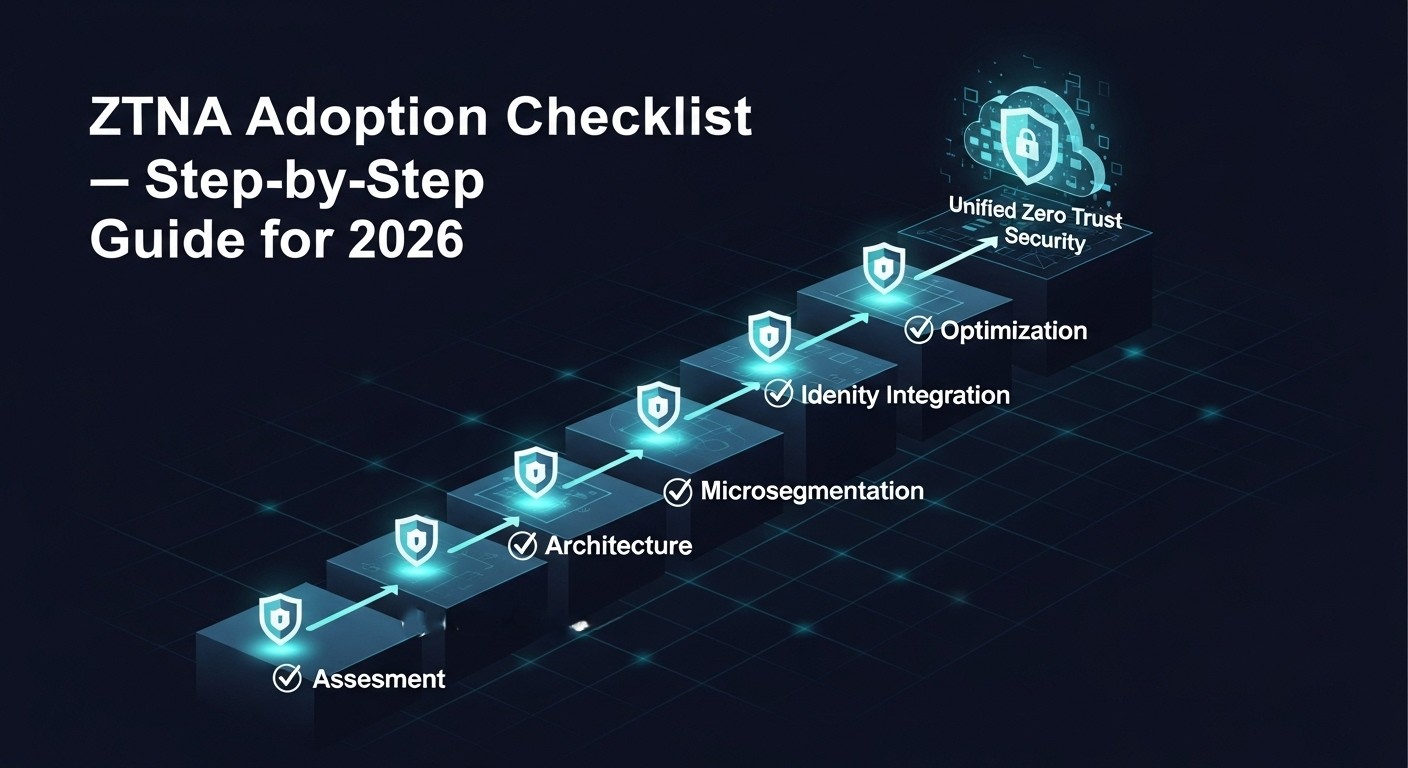
ZTNA Adoption Checklist for 2026: Step-by-Step Guide for Secure Implementation
Table of Contents
- Introduction: Why ZTNA Implementation Matters
- Step 1: Define Objectives and Scope
- Step 2: Assess Current Access and Security Infrastructure
- Step 3: Design the ZTNA Architecture
- Step 4: Integrate Identity and Access Management (IAM)
- Step 5: Incorporate Microsegmentation and SASE
- Step 6: Pilot Deployment and Policy Refinement
- Step 7: Monitor, Optimize, and Scale
- Frequently Asked Questions
- Related Reading
Introduction: Why ZTNA Implementation Matters
As hybrid work and cloud migration accelerate, traditional perimeter-based security models can no longer protect distributed users and data. Zero Trust Network Access (ZTNA) has emerged as the foundation of modern security, verifying every connection dynamically and minimizing exposure to lateral movement.
However, implementing ZTNA requires structured planning. This checklist provides a practical roadmap to help organizations transition from legacy VPNs and fragmented access controls to a unified Zero Trust framework by 2026.
Secure your business and remote users
Deploy the SecureTrust stack, reduce lateral movement, and monitor every endpoint, fully managed for you.
Book a Meeting NowStep 1: Define Objectives and Scope
Before choosing tools or vendors, clarify the purpose of your ZTNA adoption. Identify what problems you aim to solve and which areas of your environment will be included in the initial rollout.
- Establish business goals (e.g., secure hybrid work, meet compliance standards, or replace VPNs)
- Define success metrics: visibility, reduced breach risk, or simplified access management
- Determine which users, apps, and devices fall under the initial implementation phase
Step 2: Assess Current Access and Security Infrastructure
Conduct a gap assessment to understand where your existing systems fall short. Many organizations rely on VPNs, legacy firewalls, and siloed identity solutions that don’t provide continuous verification.
- Inventory current access technologies, identity providers, and network configurations
- Identify high-risk zones such as unmanaged devices, remote access tunnels, and shadow IT
- Document existing security policies and user roles to align them with Zero Trust principles
For context, see Zero Trust vs. Legacy VPN: Choosing the Right Access Solution for 2026.
Step 3: Design the ZTNA Architecture
Build a Zero Trust architecture that aligns with your operational model. Consider scalability, policy granularity, and integration with existing IT workflows.
- Choose between agent-based or agentless ZTNA models based on device management needs
- Design traffic flow for both remote and on-premise users
- Incorporate segmentation to minimize lateral movement
- Plan for policy enforcement via a cloud-native or hybrid control plane
Learn more about ZTNA design principles in Unified ZTNA 2025: Stopping Lateral Movement with Zero Trust Network Access.
Step 4: Integrate Identity and Access Management (IAM)
ZTNA success depends on strong identity foundations. Integration with your Identity Provider (IdP) enables centralized authentication and continuous access validation.
- Adopt Single Sign-On (SSO) and Multi-Factor Authentication (MFA)
- Use conditional access policies based on user risk, device posture, and location
- Connect ZTNA enforcement points with your IAM for unified policy control
Step 5: Incorporate Microsegmentation and SASE
To ensure complete isolation and control, integrate Microsegmentation Fundamentals into your Zero Trust rollout. Segment workloads and applications to restrict east-west traffic within your environment.
Combine ZTNA with a SASE (Secure Access Service Edge) platform to centralize management and enforce policies through the cloud edge. This approach unifies secure access, performance optimization, and global scalability.
Step 6: Pilot Deployment and Policy Refinement
Begin with a pilot deployment covering a limited set of users and applications. Validate identity mapping, access enforcement, and policy behavior under real-world conditions.
- Monitor user experience and connection performance
- Adjust access rules to balance security and usability
- Expand coverage gradually, ensuring consistency across all environments
Step 7: Monitor, Optimize, and Scale
Zero Trust is not a one-time project. Continuous monitoring and adaptation are key to maintaining protection as your infrastructure evolves.
- Use analytics and XDR/SIEM data to detect anomalies and refine policies
- Review user access logs regularly to enforce least privilege
- Integrate automated incident response and MFA re-prompts for suspicious activity
- Conduct quarterly reviews to measure progress against business goals
Frequently Asked Questions
How long does it take to deploy ZTNA?
Small deployments can be completed in weeks, while enterprise rollouts may take several months depending on the number of users, applications, and integrations required.
Does ZTNA replace VPNs entirely?
Yes. ZTNA provides more secure, scalable, and context-aware access without the broad exposure of VPN tunnels.
Can ZTNA improve compliance?
Absolutely. Continuous authentication, detailed logging, and granular access controls support HIPAA, PCI DSS, and NIST requirements.