Zero Trust vs. Legacy VPN: Choosing the Right Access Solution for 2026
Table of Contents
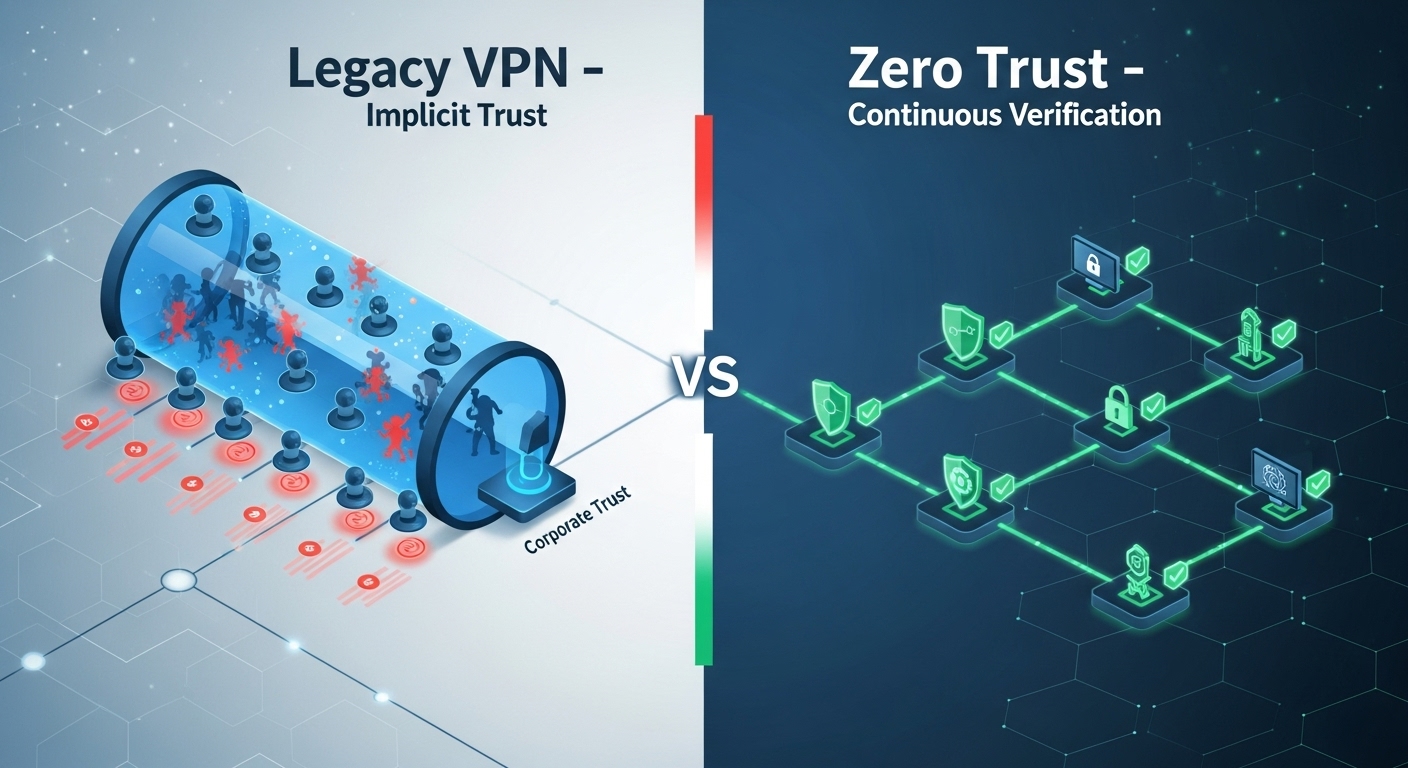
The Evolution of Remote Access Security
The traditional VPN model once served as the backbone of remote access security, creating encrypted tunnels between users and corporate networks. However, the explosion of hybrid work, SaaS applications, and unmanaged devices has rendered this perimeter-centric approach obsolete. In 2026, the focus has shifted toward Zero Trust Network Access (ZTNA), a model built on continuous verification and least privilege access rather than implicit trust.
Understanding the Limitations of VPNs
VPNs assume that once a user authenticates, they can be trusted across the internal network. This design creates a single point of failure — a compromised credential or endpoint can lead to unrestricted lateral movement. Performance degradation, inconsistent user experience, and limited visibility further undermine VPN effectiveness in modern distributed environments.
Secure your business and remote users
Deploy the SecureTrust stack, reduce lateral movement, and monitor every endpoint, fully managed for you.
Book a Meeting Now- Implicit trust within network boundaries
- Lack of continuous authentication and risk evaluation
- Inability to segment access at the application level
- Performance bottlenecks due to centralized routing
- Limited scalability for hybrid and multi-cloud architectures
Why Zero Trust Network Access (ZTNA) Surpasses VPNs
ZTNA replaces the “connect first, verify later” model with a dynamic, identity-driven approach. Every access request is continuously authenticated and authorized based on user identity, device posture, and behavioral context. ZTNA grants session-based access only to specific applications, never exposing the broader network. This shift dramatically reduces attack surface and eliminates the lateral spread that typically follows VPN compromise.
Key Differences Between ZTNA and VPN
| Feature | Legacy VPN | Zero Trust Network Access (ZTNA) |
|---|---|---|
| Trust Model | Implicit after login | Continuous verification per request |
| Access Scope | Network-level (broad) | Application-level (granular) |
| Visibility | Limited after connection | Full session and user activity monitoring |
| Attack Surface | Large, enables lateral movement | Minimal, isolates each session |
| Scalability | Hardware or site-dependent | Cloud-native and globally distributed |
| User Experience | Latency from backhauling traffic | Optimized routing via cloud edge |
How to Transition from VPN to Zero Trust
- Start by mapping all applications and user groups
- Adopt identity-based access controls and device posture assessment
- Deploy ZTNA incrementally, focusing on high-value or high-risk assets first
- Integrate with your existing identity provider (IdP) and endpoint management systems
- Replace network-level access policies with application-level segmentation
Integrating ZTNA with SASE and XDR Platforms
ZTNA operates most effectively when combined with a Secure Access Service Edge (SASE) framework and an Extended Detection and Response (XDR) system. SASE unifies networking and security enforcement in the cloud, while XDR provides threat detection and automated incident response across endpoints, identities, and networks. Together, they deliver continuous visibility, control, and containment from access to detection.
To see how Unified ZTNA fits into this ecosystem, review our previous article on Unified Zero Trust Network Access and Lateral Movement Defense, which explains how continuous verification stops lateral movement across hybrid environments.
Frequently Asked Questions
Is ZTNA a complete replacement for VPNs?
Yes, in most modern environments. While VPNs may remain for legacy applications, ZTNA provides superior control, scalability, and security for distributed workforces.
Does ZTNA impact performance?
No. Cloud-native ZTNA solutions leverage edge-based routing and optimized connections, often improving latency compared to traditional VPN concentrators.
Can ZTNA improve compliance posture?
Absolutely. ZTNA’s granular visibility and audit trails support regulatory requirements like HIPAA, PCI DSS, and NIST 800-53 by enforcing least privilege and monitoring all session activity.